In 2013, when the NSA (United States National Security Agency) scandal was leaked to the public, people started to opt for the services which can provide them a strong privacy for their data. Among the services people opted for, most particularly for Emails, were different plug-ins and extensions for their browsers. Interestingly, among the various plug-ins and extensions that people started to use, there were two main programs that were solely responsible for the complete email security that the people needed. One was S/MIME which we will see later and the other was PGP.
As said, PGP (Pretty Good Privacy), is a popular program that is used to provide confidentiality and authentication services for electronic mail and file storage. It was designed by Phil Zimmermann way back in 1991. He designed it in such a way, that the best cryptographic algorithms such as RSA, Diffie-Hellman key exchange, DSS are used for the public-key encryption (or) asymmetric encryption; CAST-128, 3DES, IDEA are used for symmetric encryption and SHA-1 is used for hashing purposes. PGP software is an open source one and is not dependent on either the OS (Operating System) or the processor. The application is based on a few commands which are very easy to use.
The following are the services offered by PGP:
1. Authentication 2. Confidentiality 3. Compression 4. Email Compatibility 5. Segmentation
In this article, we will see about Authentication and Confidentiality.
1. Authentication:
Authentication basically means something that is used to validate something as true or real. To login into some sites sometimes we give our account name and password, that is an authentication verification procedure.
In the email world, checking the authenticity of an email is nothing but to check whether it actually came from the person it says. In emails, authentication has to be checked as there are some people who spoof the emails or some spams and sometimes it can cause a lot of inconvenience. The Authentication service in PGP is provided as follows:
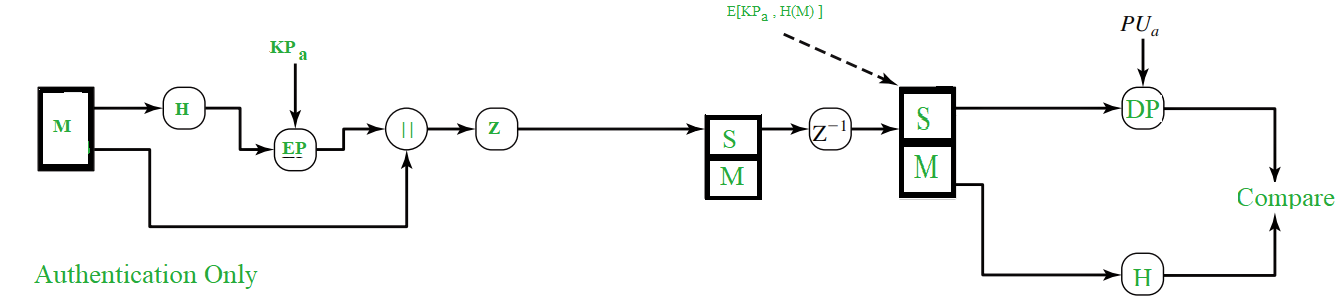
As shown in the above figure, the Hash Function (H) calculates the Hash Value of the message. For the hashing purpose, SHA-1 is used and it produces a 160 bit output hash value. Then, using the sender’s private key (KPa), it is encrypted and it’s called as Digital Signature. The Message is then appended to the signature. All the process happened till now, is sometimes described as signing the message . Then the message is compressed to reduce the transmission overhead and is sent over to the receiver.
At the receiver’s end, the data is decompressed and the message, signature are obtained. The signature is then decrypted using the sender’s public key(PUa) and the hash value is obtained. The message is again passed to hash function and it’s hash value is calculated and obtained.
Both the values, one from signature and another from the recent output of hash function are compared and if both are same, it means that the email is actually sent from a known one and is legit, else it means that it’s not a legit one.
2. Confidentiality:
Sometimes we see some packages labelled as ‘Confidential’, which means that those packages are not meant for all the people and only selected persons can see them. The same applies to the email confidentiality as well. Here, in the email service, only the sender and the receiver should be able to read the message, that means the contents have to be kept secret from every other person, except for those two.
PGP provides that Confidentiality service in the following manner:
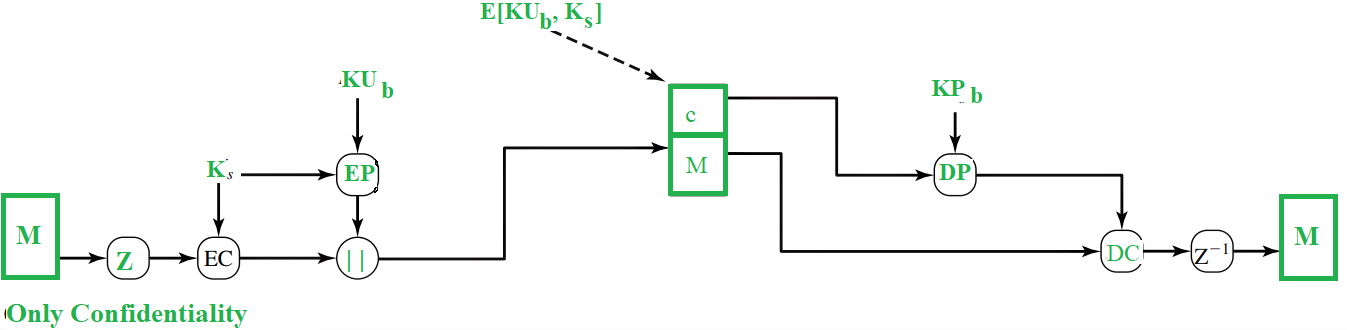
The message is first compressed and a 128 bit session key (Ks), generated by the PGP, is used to encrypt the message through symmetric encryption. Then, the session key (Ks) itself gets encrypted through public key encryption (EP) using receiver’s public key(KUb) . Both the encrypted entities are now concatenated and sent to the receiver.
As you can see, the original message was compressed and then encrypted initially and hence even if any one could get hold of the traffic, he cannot read the contents as they are not in readable form and they can only read them if they had the session key (Ks). Even though session key is transmitted to the receiver and hence, is in the traffic, it is in encrypted form and only the receiver’s private key (KPb)can be used to decrypt that and thus our message would be completely safe.
At the receiver’s end, the encrypted session key is decrypted using receiver’s private key (KPb) and the message is decrypted with the obtained session key. Then, the message is decompressed to obtain the original message (M).
RSA algorithm is used for the public-key encryption and for the symmetric key encryption, CAST-128(or IDEA or 3DES) is used.
Practically, both the Authentication and Confidentiality services are provided in parallel as follows :
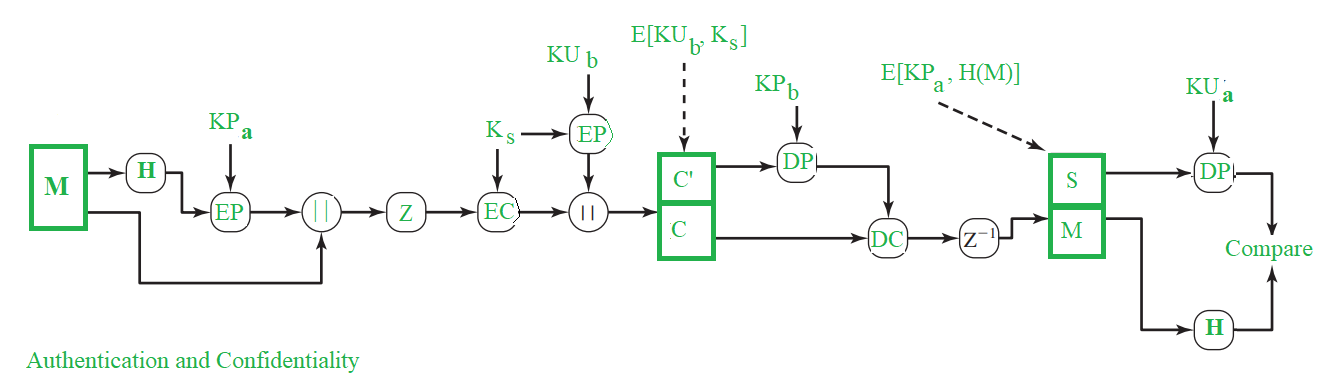
Note:
M – Message
H – Hash Function
Ks – A random Session Key created for Symmetric Encryption purpose
DP – Public-Key Decryption Algorithm
EP – Public-Key Encryption Algorithm
DC – Asymmetric Encryption Algorithm
EC – Symmetric Encryption Algorithm
KPb – A private key of user B used in Public-key encryption process
KPa – A private key of user A used in Public-key encryption process
PUa – A public key of user A used in Public-key encryption process
PUb – A public key of user B used in Public-key encryption process
|| – Concatenation
Z – Compression Function
Z-1 – Decompression Function
Kerberos
Kerberos provides a centralized authentication server whose function is to authenticate users to servers and servers to users. In Kerberos Authentication server and database is used for client authentication. Kerberos runs as a third-party trusted server known as the Key Distribution Center (KDC). Each user and service on the network is a principal.
The main components of Kerberos are:
- Authentication Server (AS):
The Authentication Server performs the initial authentication and ticket for Ticket Granting Service.
- Database:
The Authentication Server verifies the access rights of users in the database.
- Ticket Granting Server (TGS):
The Ticket Granting Server issues the ticket for the Server
Kerberos Overview:
- Step-1:
User login and request services on the host. Thus user requests for ticket-granting service.
- Step-2:
Authentication Server verifies user’s access right using database and then gives ticket-granting-ticket and session key. Results are encrypted using the Password of the user.
- Step-3:
The decryption of the message is done using the password then send the ticket to Ticket Granting Server. The Ticket contains authenticators like user names and network addresses.
- Step-4:
Ticket Granting Server decrypts the ticket sent by User and authenticator verifies the request then creates the ticket for requesting services from the Server.
- Step-5:
The user sends the Ticket and Authenticator to the Server.
- Step-6:
The server verifies the Ticket and authenticators then generate access to the service. After this User can access the services.
Kerberos Limitations
- Each network service must be modified individually for use with Kerberos
- It doesn’t work well in a timeshare environment
- Secured Kerberos Server
- Requires an always-on Kerberos server
- Stores all passwords are encrypted with a single key
- Assumes workstations are secure
- May result in cascading loss of trust.
- Scalability
Is Kerberos Infallible?
No security measure is 100% impregnable, and Kerberos is no exception. Because it’s been around for so long, hackers have had the ability over the years to find ways around it, typically through forging tickets, repeated attempts at password guessing (brute force/credential stuffing), and the use of malware, to downgrade the encryption.
Despite this, Kerberos remains the best access security protocol available today. The protocol is flexible enough to employ stronger encryption algorithms to combat new threats, and if users employ good password-choice guidelines, you shouldn’t have a problem!
What is Kerberos Used For?
Although Kerberos can be found everywhere in the digital world, it is commonly used in secure systems that rely on robust authentication and auditing capabilities. Kerberos is used for Posix, Active Directory, NFS, and Samba authentication. It is also an alternative authentication system to SSH, POP, and SMTP.

కామెంట్లు లేవు:
కామెంట్ను పోస్ట్ చేయండి